Active MITM Attack Simulation Using XAMPP and Burp Suite
Simulated an active MITM attack between a Windows server and an Ubuntu client to intercept and modify web traffic using XAMPP and Burp Suite, demonstrating risks to confidentiality and integrity of communication. The project highlighted practical techniques for detecting and preventing such attacks.
Steps
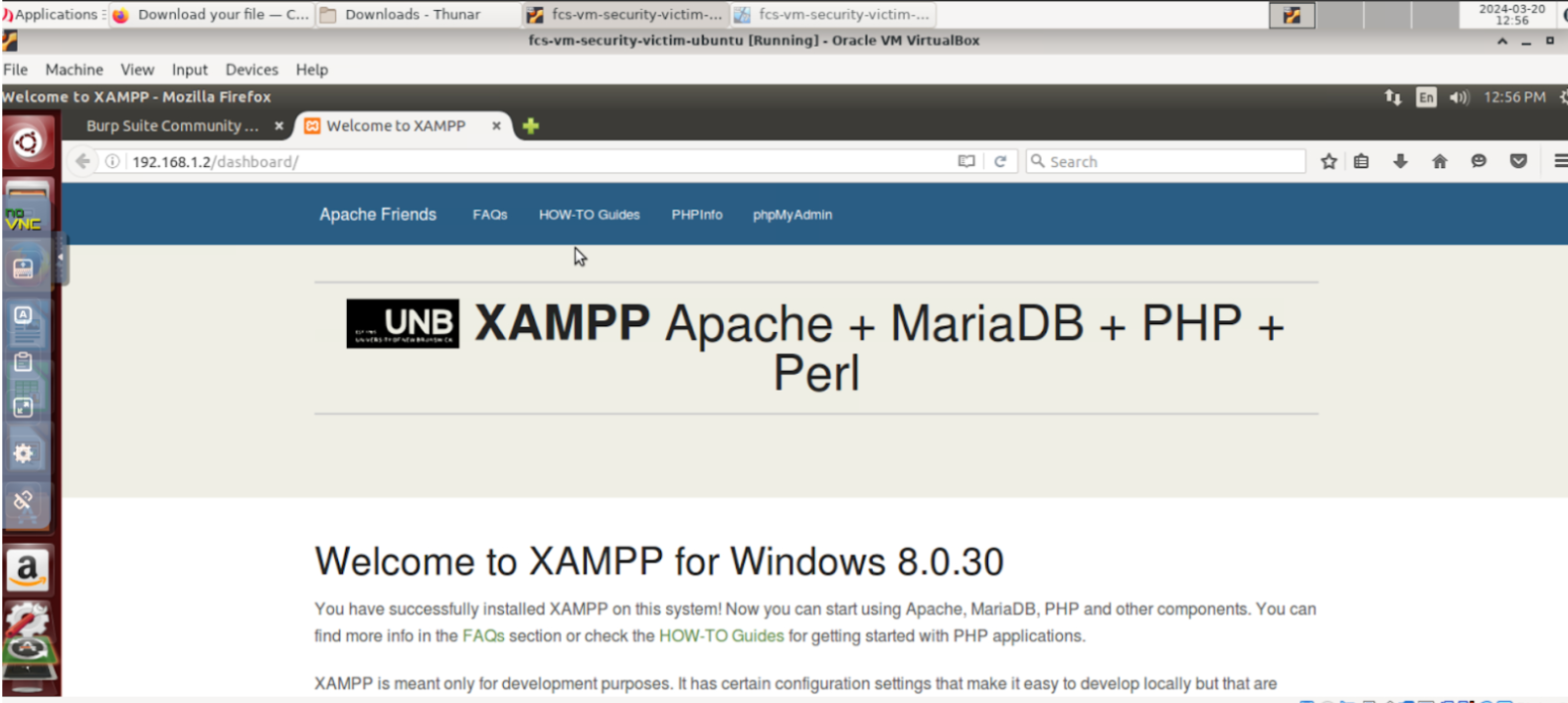
Step 1: Disabled Windows Firewall on the Windows VM, installed XAMPP with Apache, and started the web server. Accessed the server from the Ubuntu VM via http://192.168.1.2 to confirm proper setup.
Step 2: Downloaded and installed Burp Suite Community Edition on the Windows VM. Launched a temporary project, added a proxy listener on IP 192.168.1.2, Port 8080, and ensured 'Intercept' was off to allow traffic flow.
Step 3: Set the Ubuntu browser to use 192.168.1.2:8080 as HTTP proxy, enabling web traffic to pass through Burp Suite for interception and analysis.
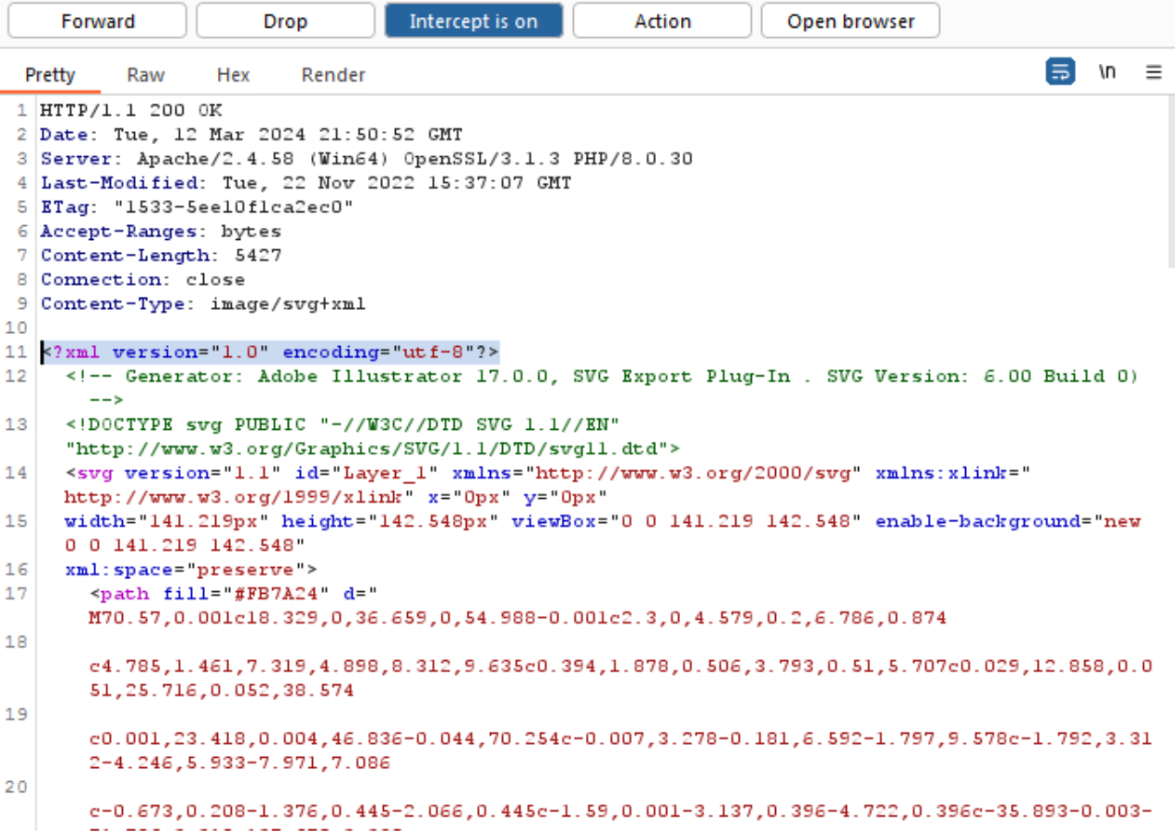
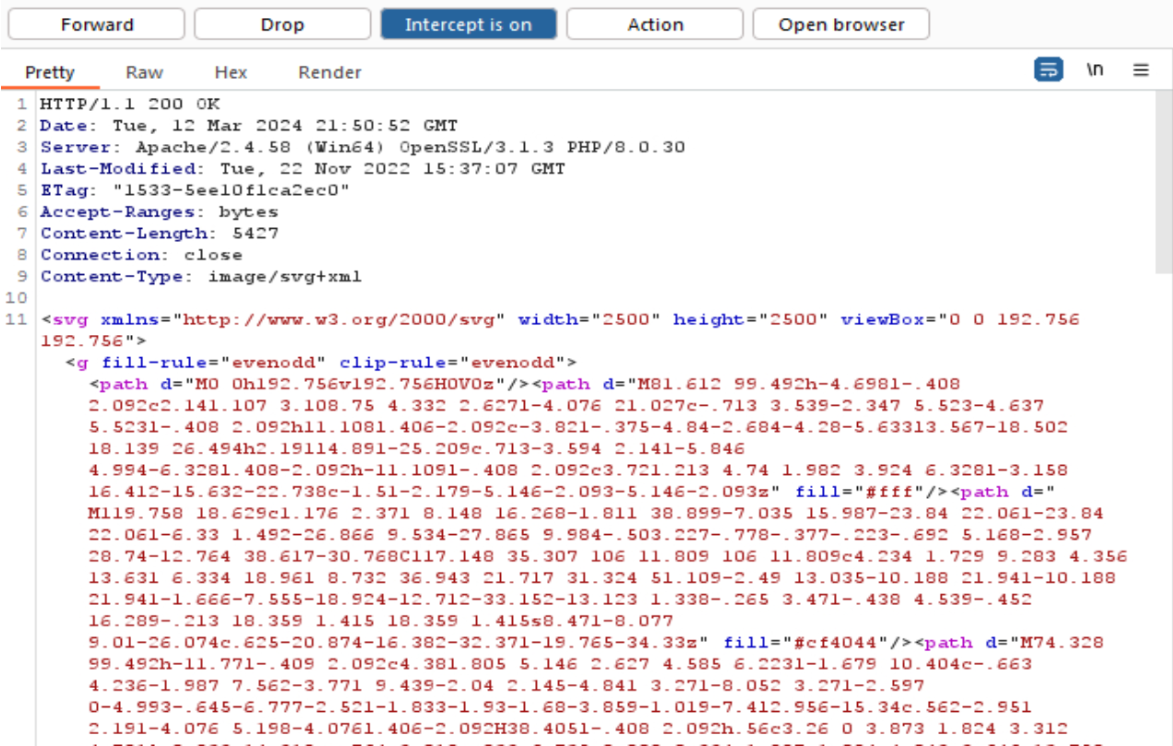
Step 4: Enabled interception in Burp Suite, captured HTTP requests and responses, modified content in real-time, and forwarded it to the browser to demonstrate that the MITM attack successfully altered communication.
Step 5: Observed how attackers could intercept and manipulate sensitive data. Implemented recommendations to mitigate MITM attacks, including enforcing HTTPS, HSTS, monitoring traffic, and avoiding untrusted networks.
Tools
XAMPP, Burp Suite Community Edition, Windows Firewall, Ubuntu Browser
Frameworks
OWASP Testing Guide, PTES
Standards
ISO 27001, NIST CSF
Findings & Recommendations
Findings:
- MITM attacks allowed interception, monitoring, and modification of communication between systems.
- Sensitive data such as passwords or personal information could have been compromised if traffic was unencrypted.
Recommendations:
- Using HTTPS with valid SSL/TLS certificates to encrypt communication.
- Implement HTTP Strict Transport Security (HSTS) to prevent protocol downgrade attacks.
- Employ network monitoring tools to detect unusual traffic patterns.
- Avoid using untrusted networks for sensitive communications.