Penetration Testing with Nmap and Metasploit
Performed a penetration testing capstone project for a new trading company to identify vulnerabilities in target systems. The project used Nmap for port scanning and Metasploit for exploit testing, demonstrating how attackers could gain access and how security teams can prevent such attacks.
Steps
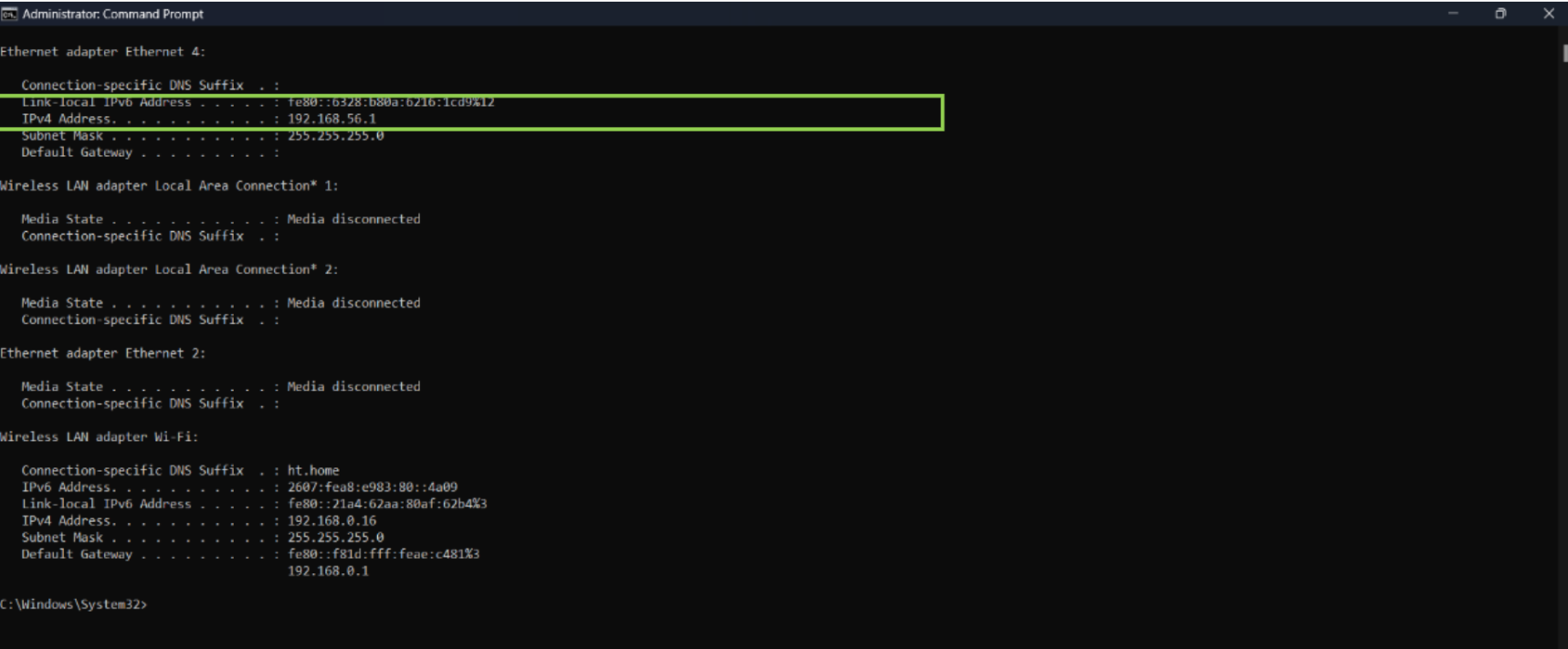
Step 1: Checked the IP address of the target computer using the ipconfig command to ensure proper network identification.
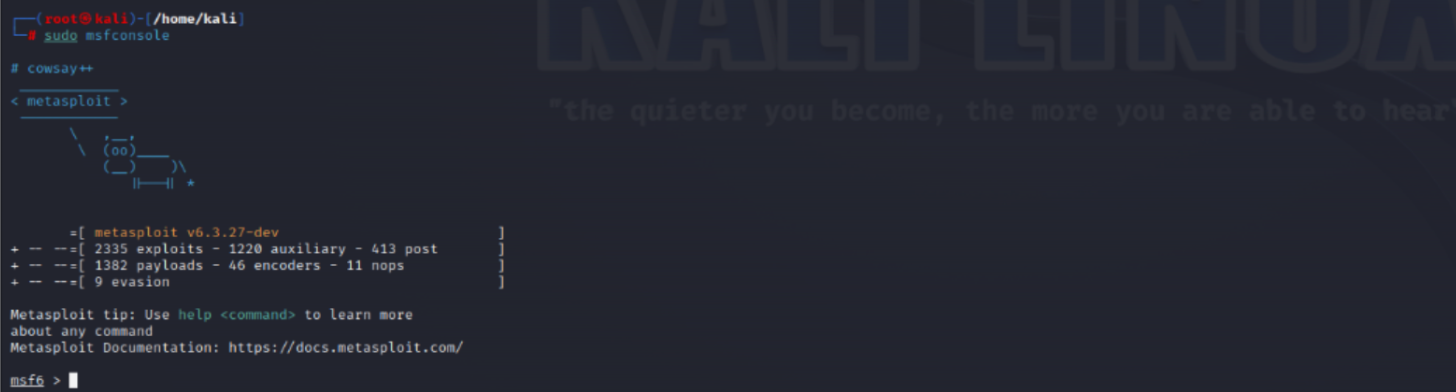
Step 2: Logged into Kali Linux on the virtual machine to prepare the penetration testing environment.
Step 3: Used Nmap to scan the target IP address, identified open ports, and traced possible attack vectors.
Step 4: Ran Metasploit using 'sudo msfconsole' to begin searching for exploits and payloads relevant to the discovered ports.
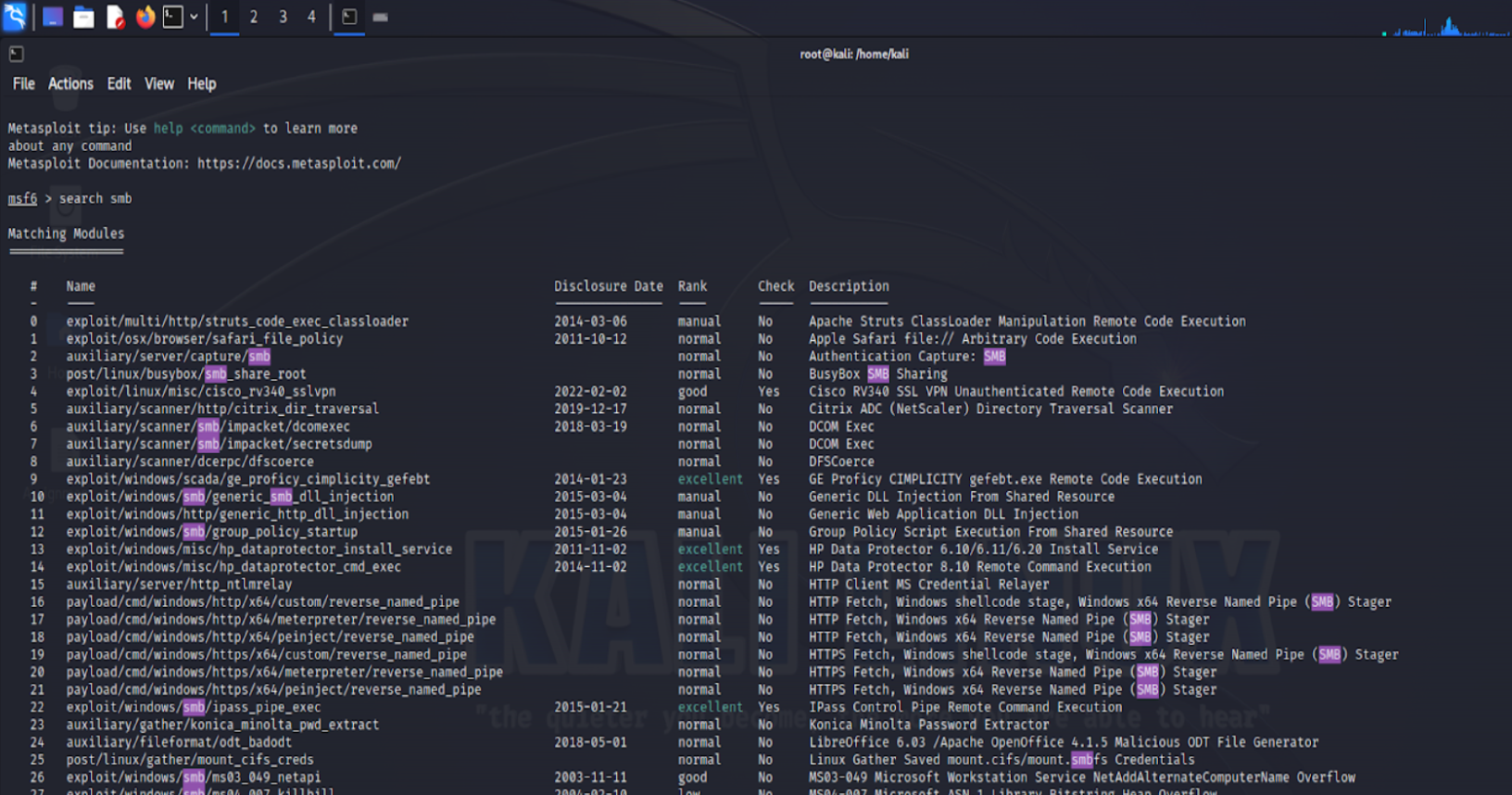
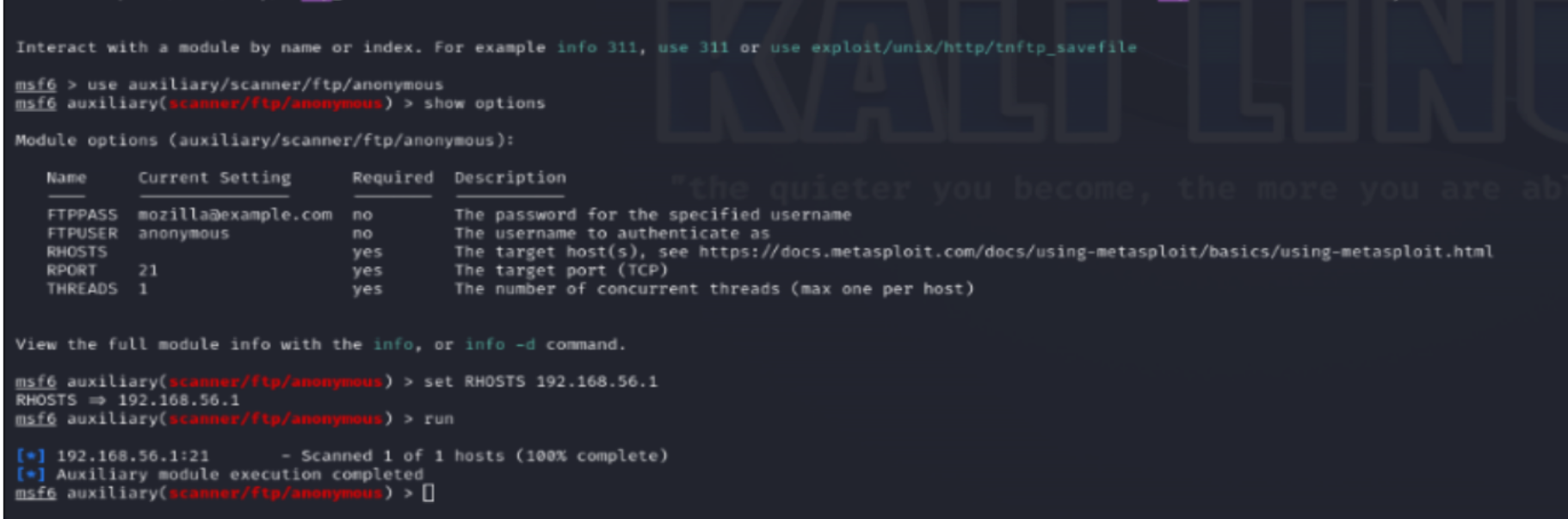
Step 5: Used the Metasploit 'search' command to find exploit, payload, and auxiliary modules that could be used against the target system.
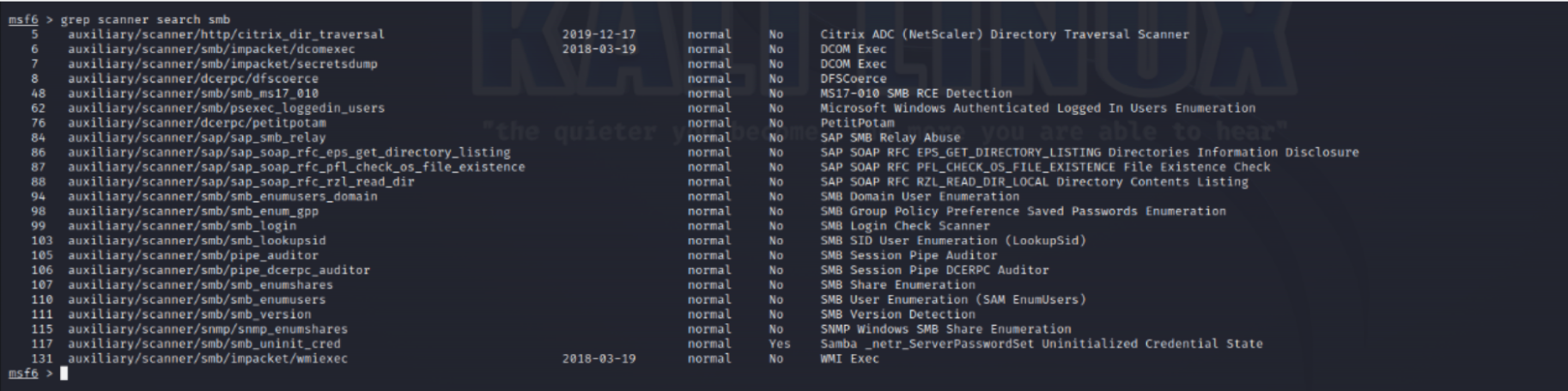
Step 6: Filtered search results using the 'grep' command to narrow down the most relevant exploit module for the target system.
Step 7: Selected a module from the search results using the 'use <module_name>' command, then ran 'show options' to view configurable parameters.
Step 8: Configured required parameters, including setting the RHOST option to the target IP address, ensuring the exploit targeted the correct system.
Step 9: Ran the exploit and observed the system's response to determine if it was vulnerable and exploitable.
Tools
Nmap, Metasploit Framework, Kali Linux, ipconfig
Frameworks
PTES, OWASP Testing Guide
Standards
ISO 27001, NIST CSF
Findings & Recommendations
Findings:
- Two IP addresses were tested for vulnerabilities; one was exploitable, the other was secure.
- The vulnerable system showed how attackers can gain unauthorized access through open ports and misconfigured services.
Recommendations:
- Implement regular patch management.
- Close unnecessary open ports.
- Enforce least privilege on user accounts.
- Conduct periodic penetration tests to identify new vulnerabilities.