Threat Intelligence Investigation Using MISP – PupyRAT Malware Analysis
Deployed and configured MISP on Ubuntu using Docker to centralize threat intelligence. Investigated a published CIRCL event on PupyRAT malware, analyzed its behavior, and identified indicators of compromise such as command-and-control server IPs.
Steps
Step 1: Installed and configured MISP using Docker containers on an Ubuntu system to enable centralized threat intelligence sharing and analysis.
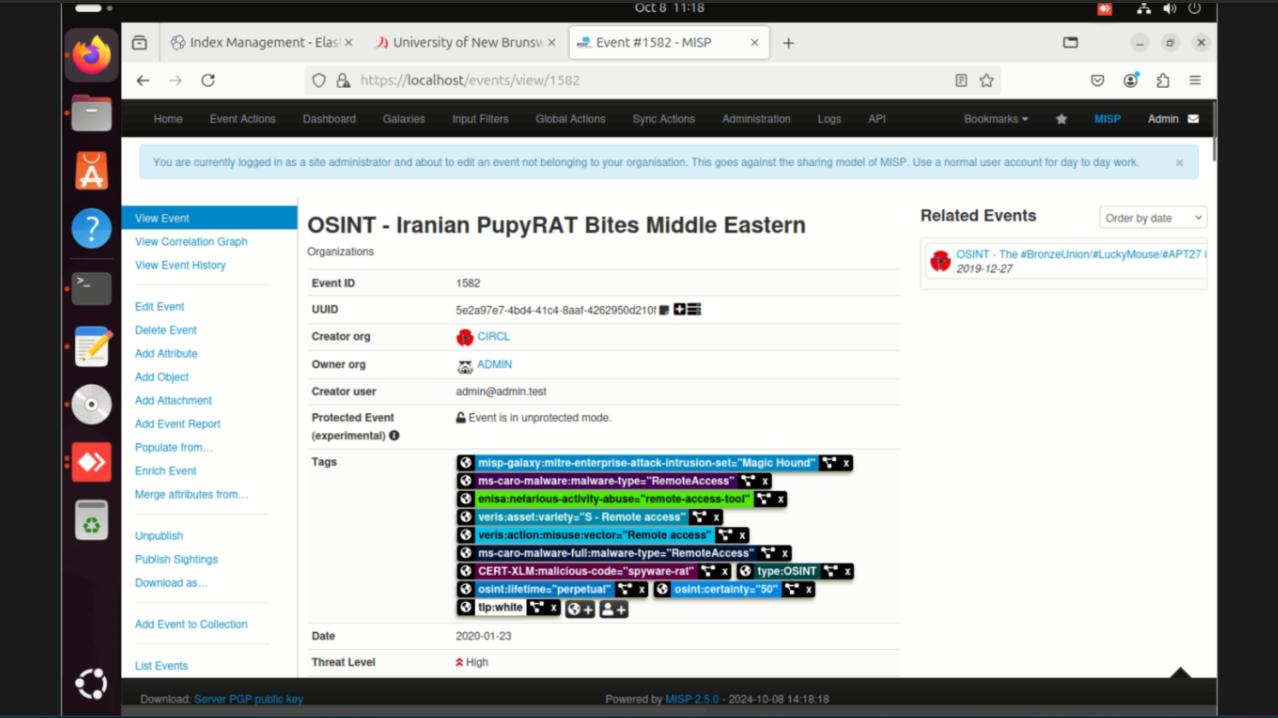
Step 2: Searched for CIRCL event ID 1582 in MISP, confirming details of the PupyRAT malware and its behavior.
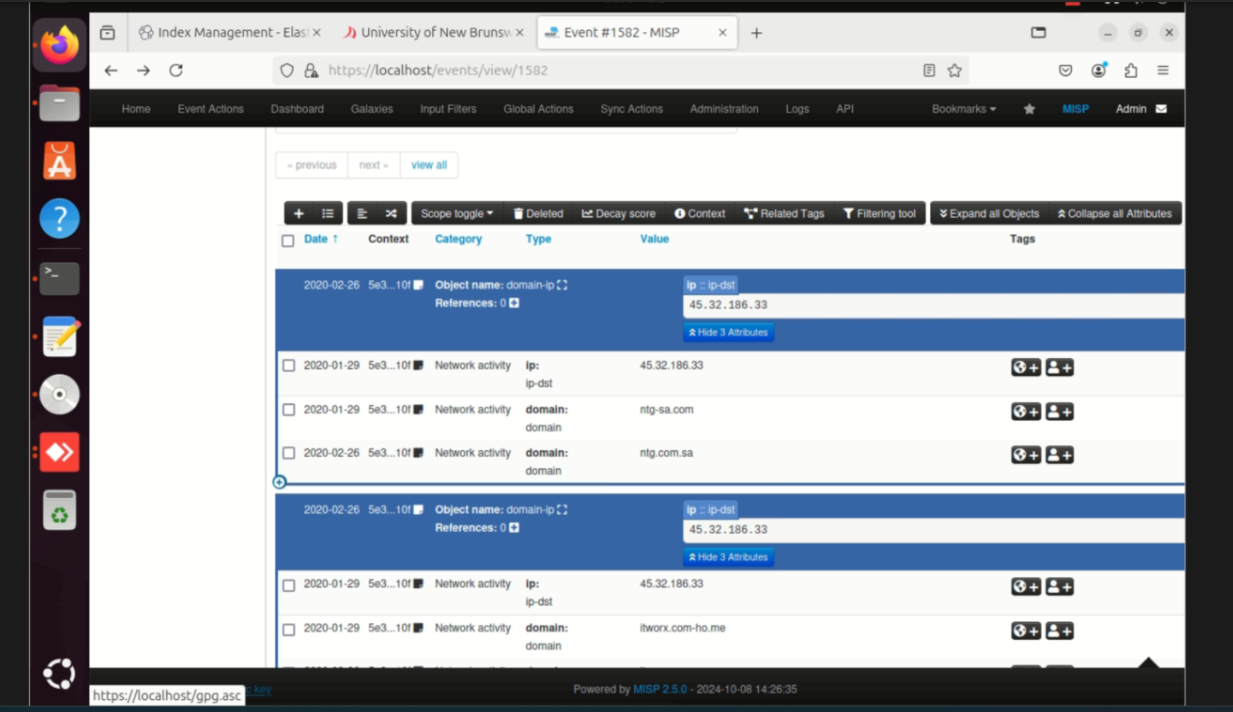
Step 3: Identified PupyRAT's command-and-control server IP (43.32.186.33) and confirmed that the malware gained ADMIN-level access to compromised systems.
Step 4: Documented IOCs (IP, behavior patterns) and mapped them to MITRE ATT&CK techniques for incident response readiness.
Tools
MISP, Docker, Ubuntu
Frameworks
Threat Intelligence Sharing, Malware Analysis
Standards
MITRE ATT&CK (TA0001 – Initial Access, TA0002 – Execution), NIST CSF (DE.CM – Security Continuous Monitoring)