Security Monitoring and Log Analysis with Splunk
Configured Splunk on Linux Ubuntu to ingest logs, analyze access patterns, and monitor system logs in real time for security events.
Steps
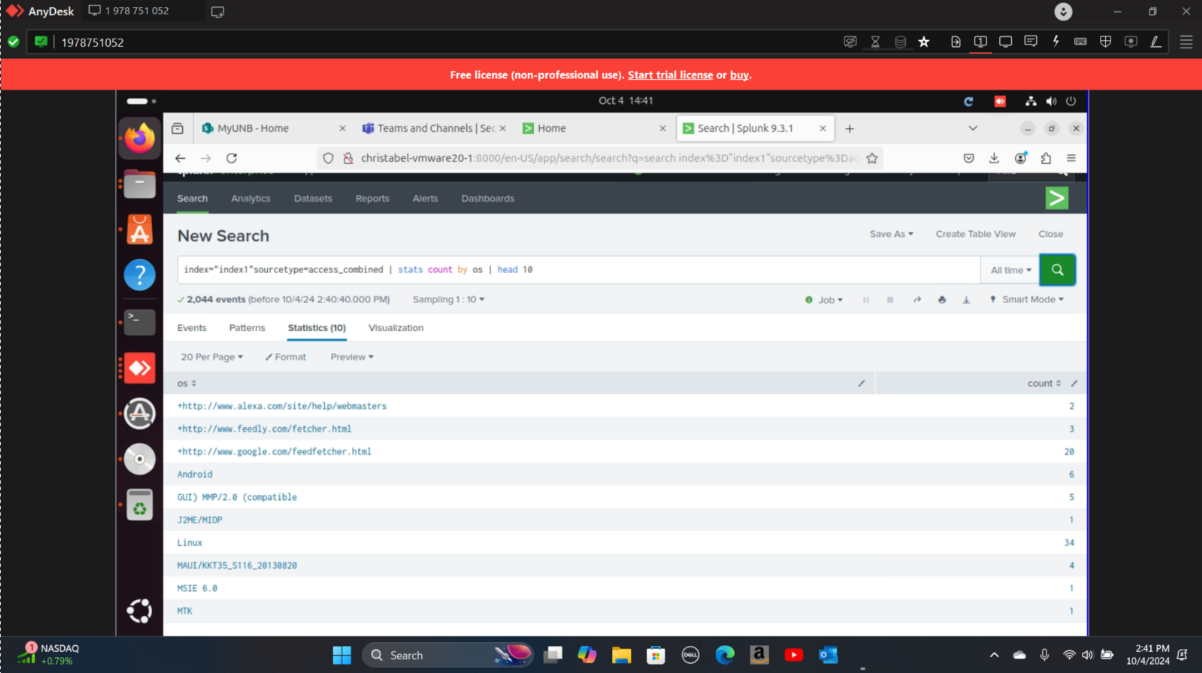
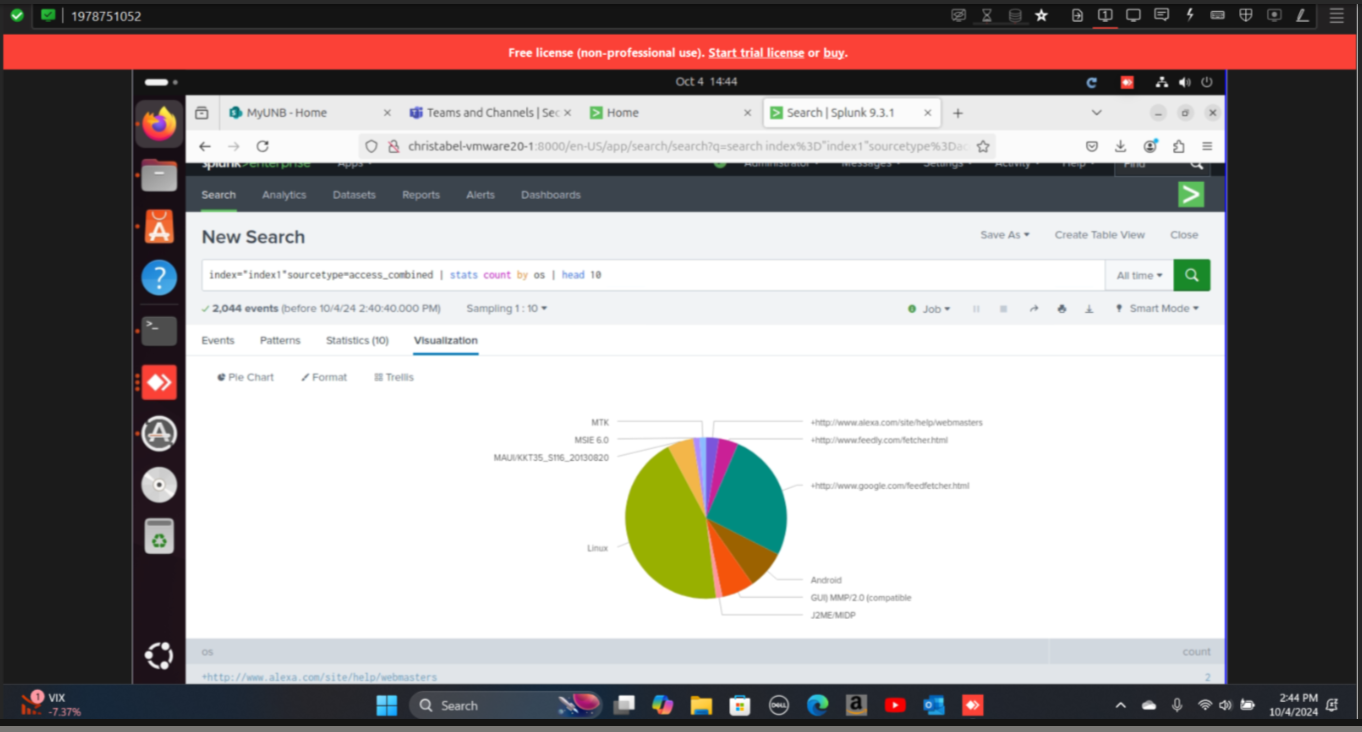
Step 1: Ingested access.log into Splunk and wrote search queries to identify the top 10 operating systems accessing the system.
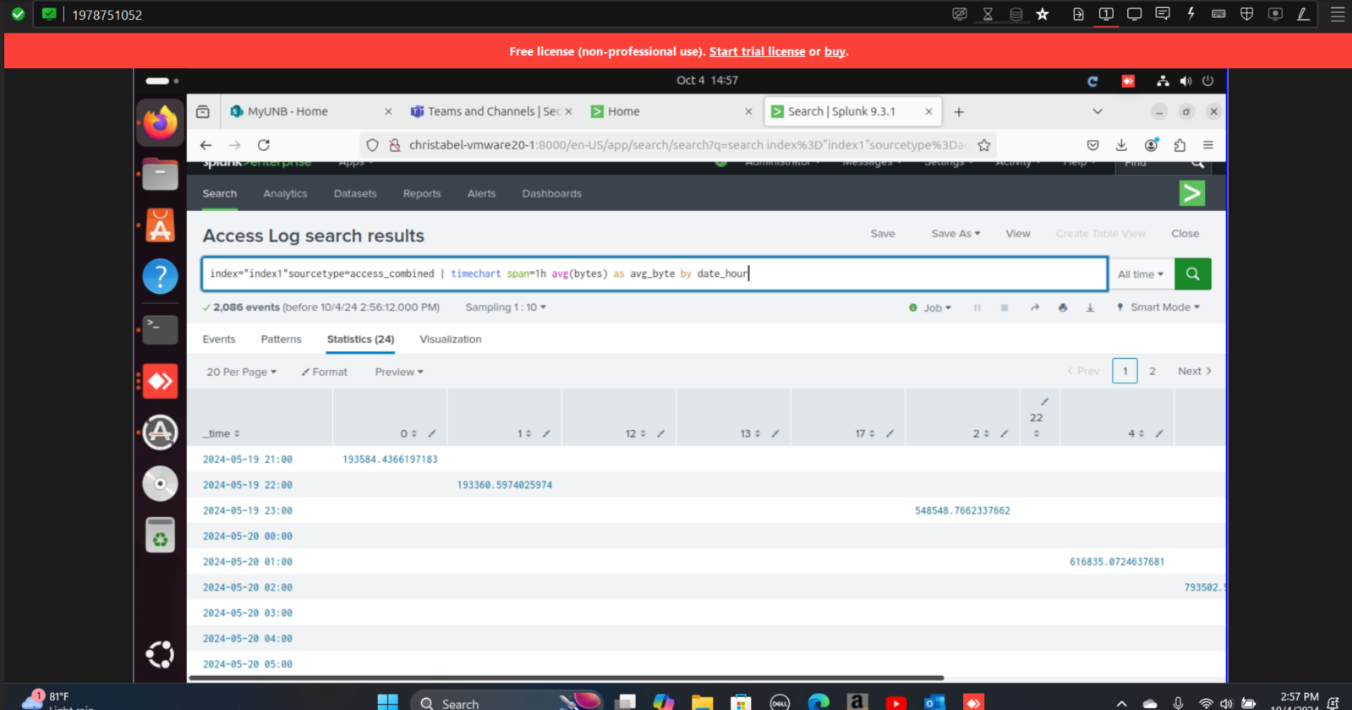
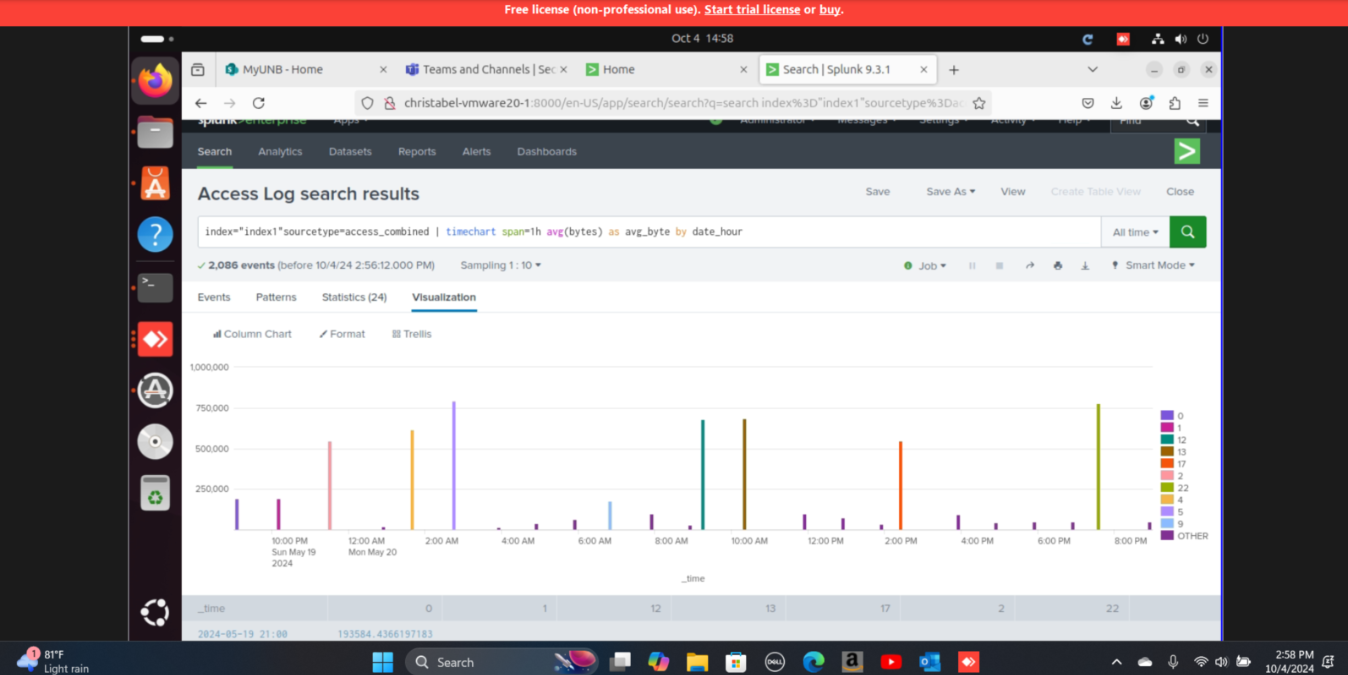
Step 2: Calculated the average byte transfer per date and hour using Splunk search queries to identify usage trends.
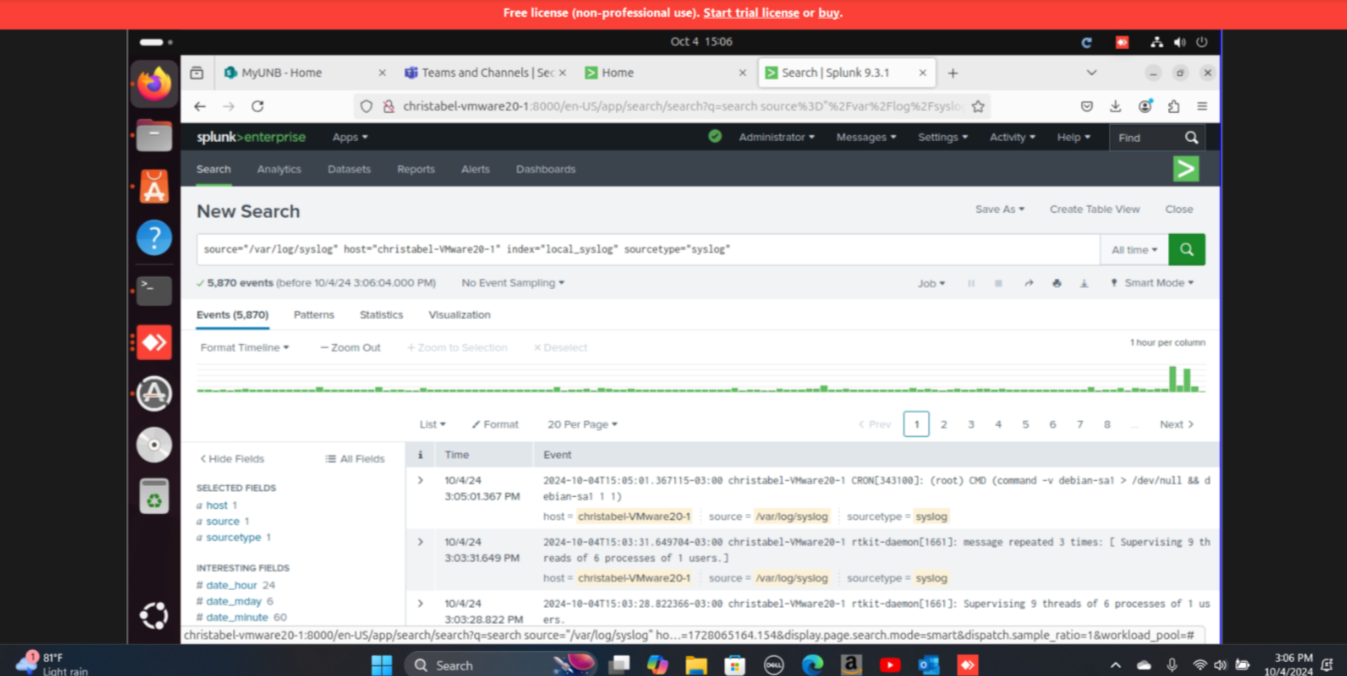
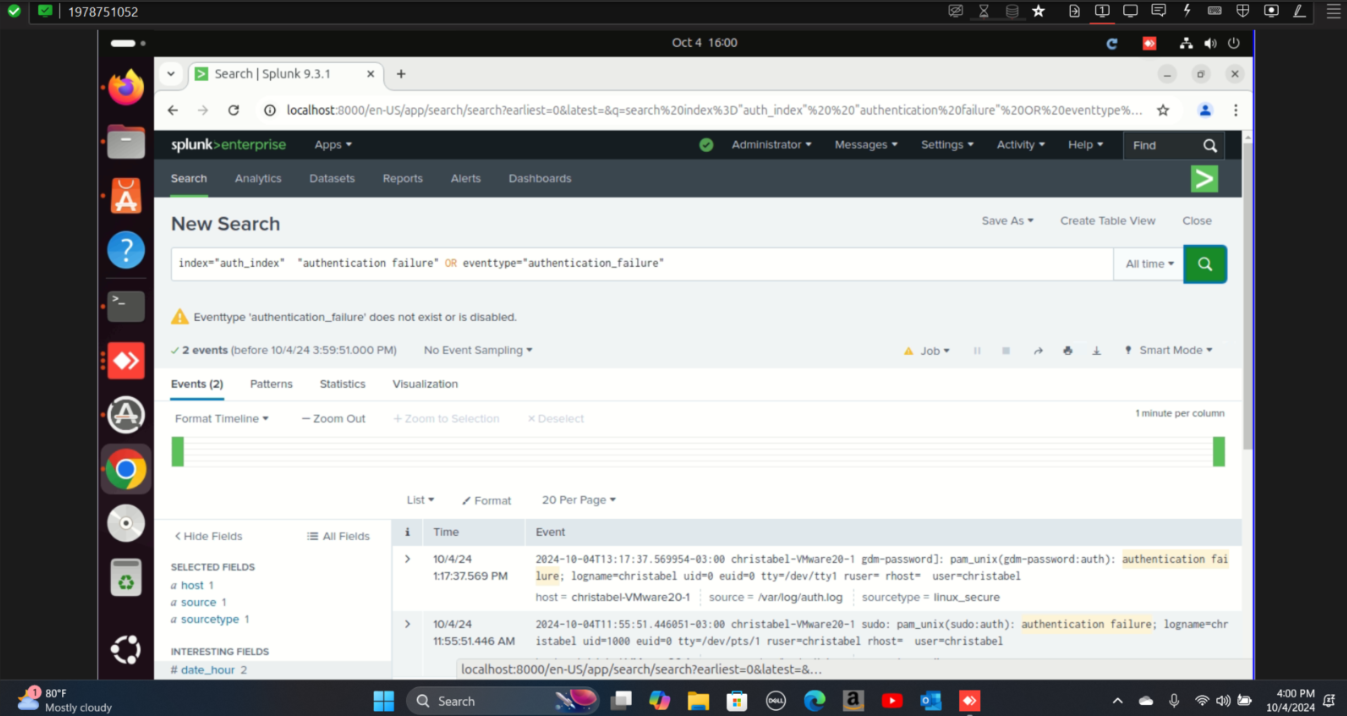
Step 3: Configured Splunk to monitor local syslog continuously and alert on suspicious security events.Also displayed results that show authentication failure.
Tools
Splunk Enterprise, Linux Ubuntu, Syslog
Frameworks
Security Information and Event Management (SIEM), Log Analysis
Standards
NIST CSF (DE.CM – Security Continuous Monitoring), ISO 27001 (A.12.4 – Logging and Monitoring)