Firewall Rule Analysis and Configuration
Analyzed inbound network traffic to a demo web server, created and tested firewall rules to allow and deny traffic, and verified the results through network logs to improve security posture.
Steps
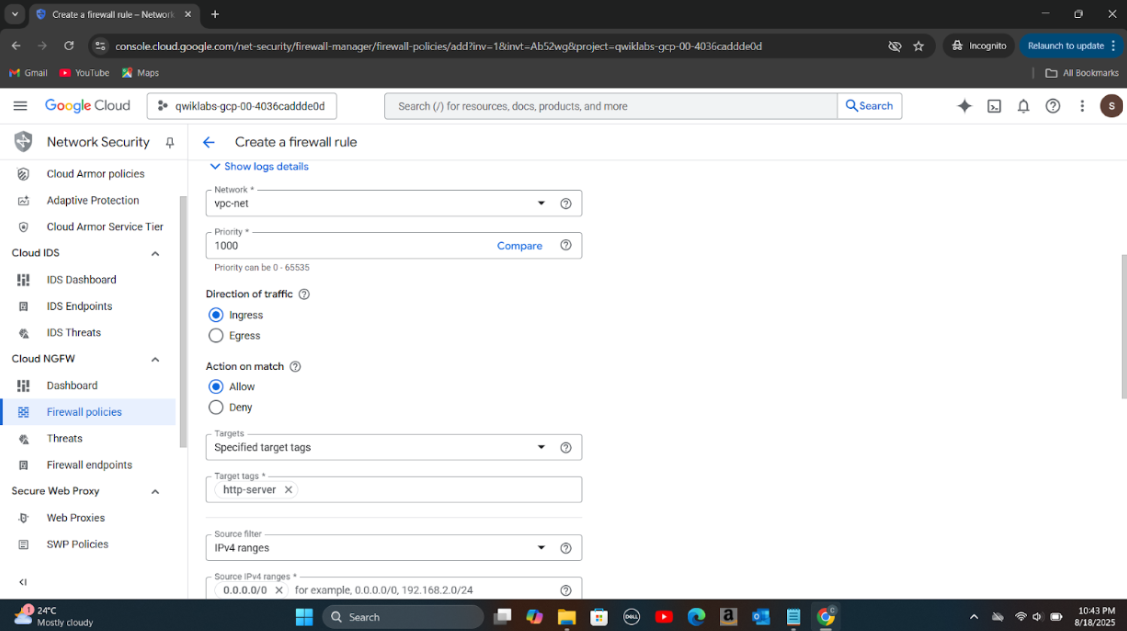
Step 1: Created a firewall rule to allow network traffic to the demo web server within the VPC network.
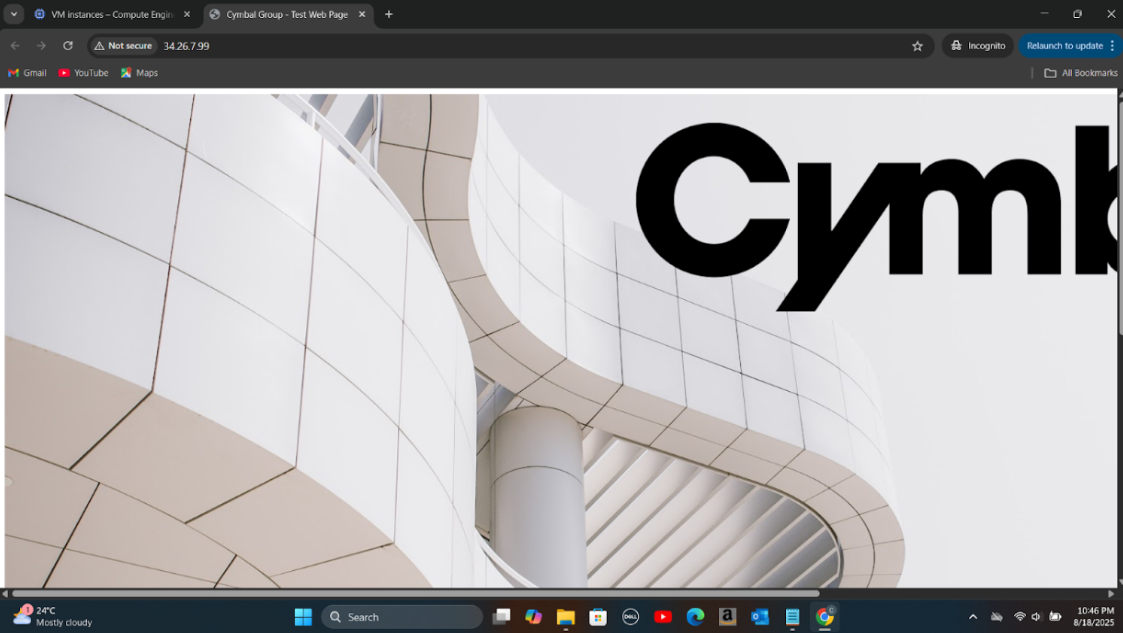
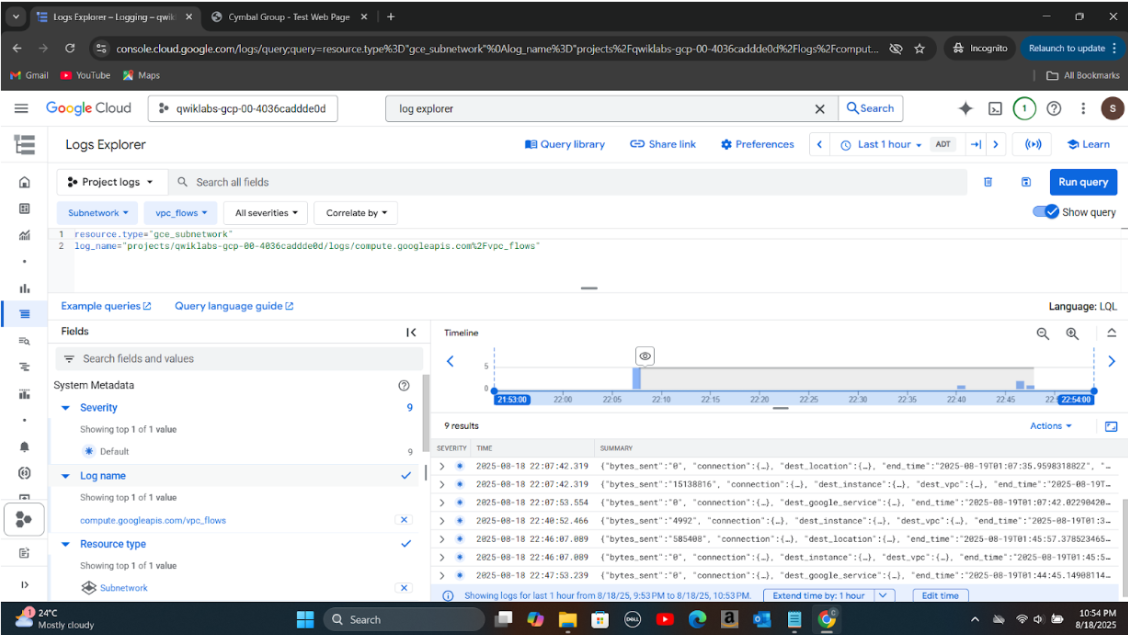
Step 2: Generated HTTP network traffic to the server and used Cloud Logging to analyze inbound connection logs.
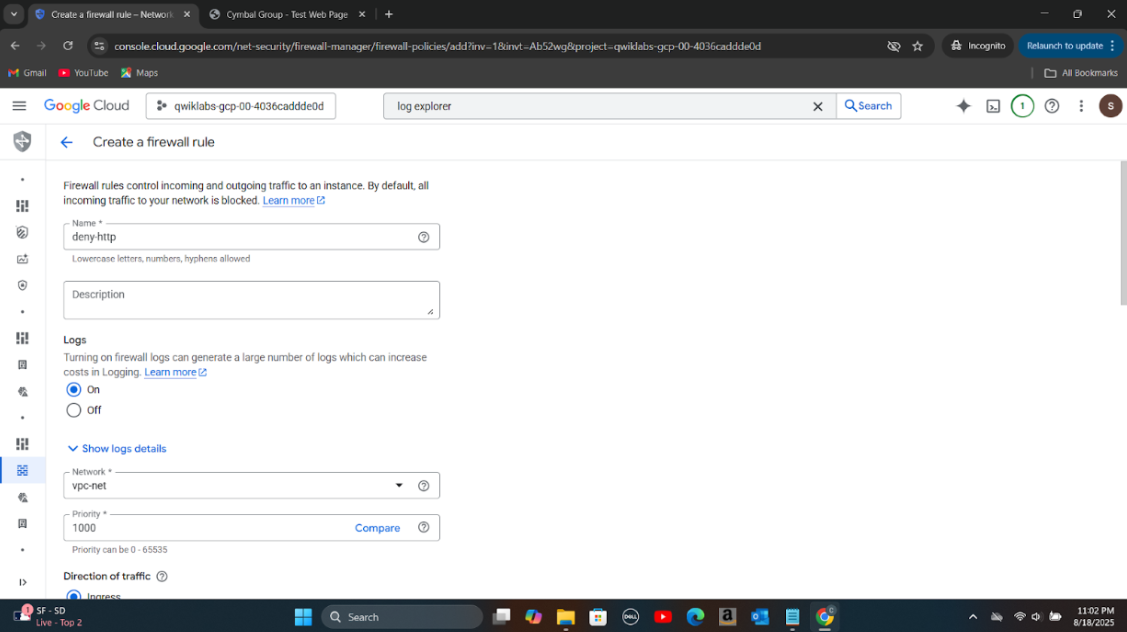
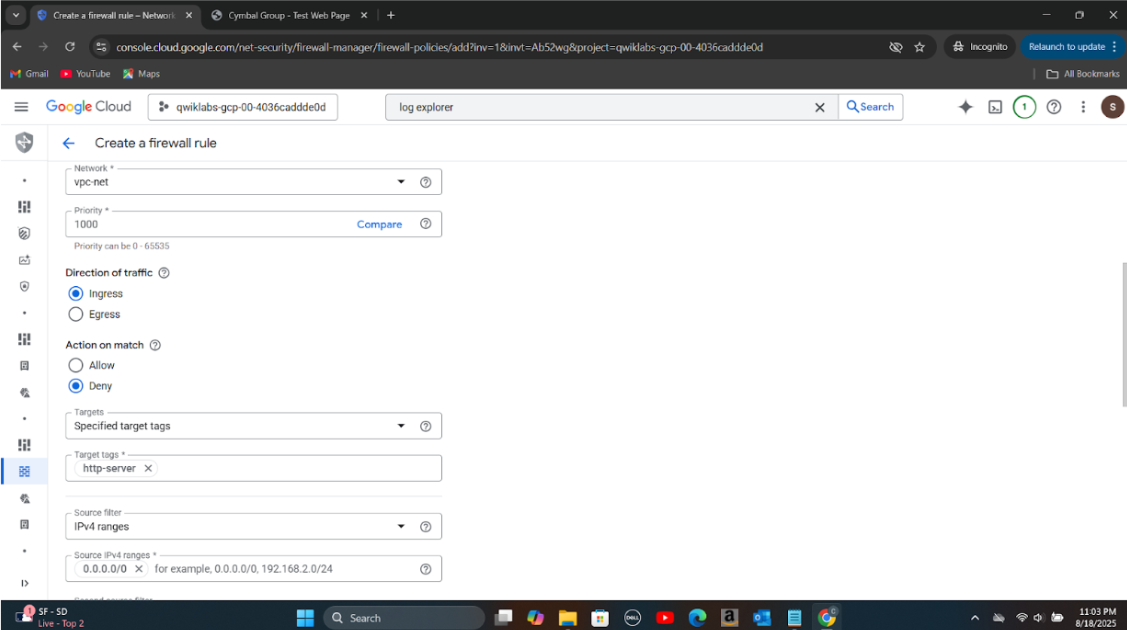
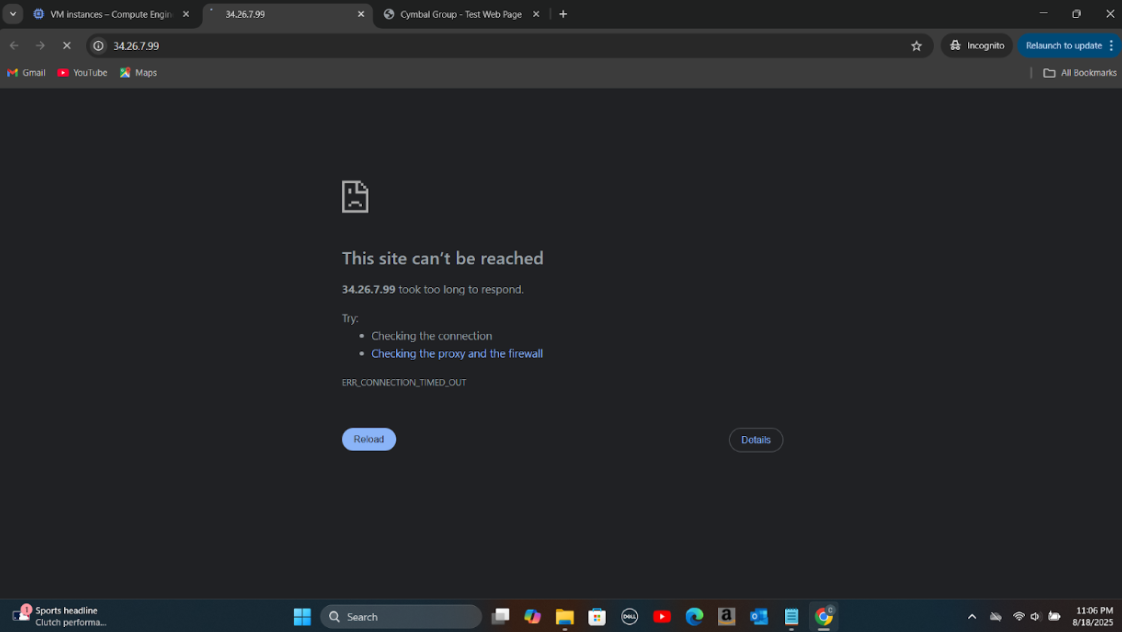
Step 3: Created a new firewall rule to deny HTTP traffic to the server and tested connectivity to confirm the block.
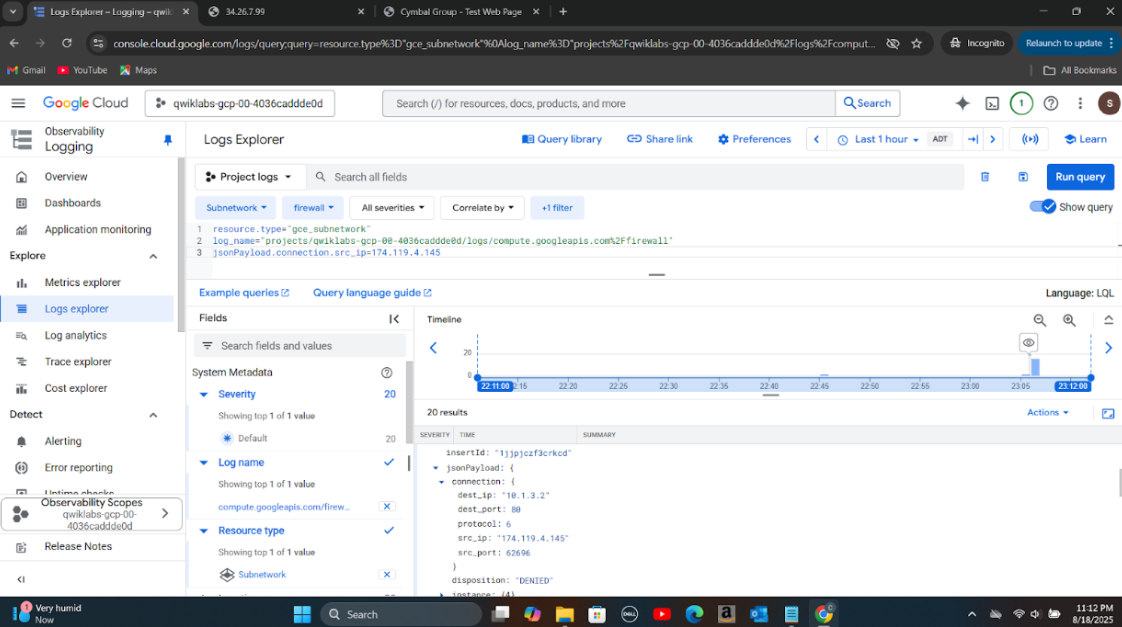
Step 4: Analyzed firewall logs again to verify that HTTP traffic was successfully blocked as per the new rule.
Tools
Google Cloud Firewall Rules, VPC Networking, Cloud Logging
Frameworks
Zero Trust Architecture, Network Security Monitoring
Standards
NIST CSF (PR.AC – Access Control, DE.CM – Continuous Monitoring), ISO 27001 (Annex A.13 – Communications Security), Cloud Security Best Practices for Firewall Configuration