Remediating a False Positive Security Alert
Recreated a service account activity that triggered a low severity security alert, analyzed the finding using Security Command Center, and remediated the issue to understand false positives and improve security policies.
Steps
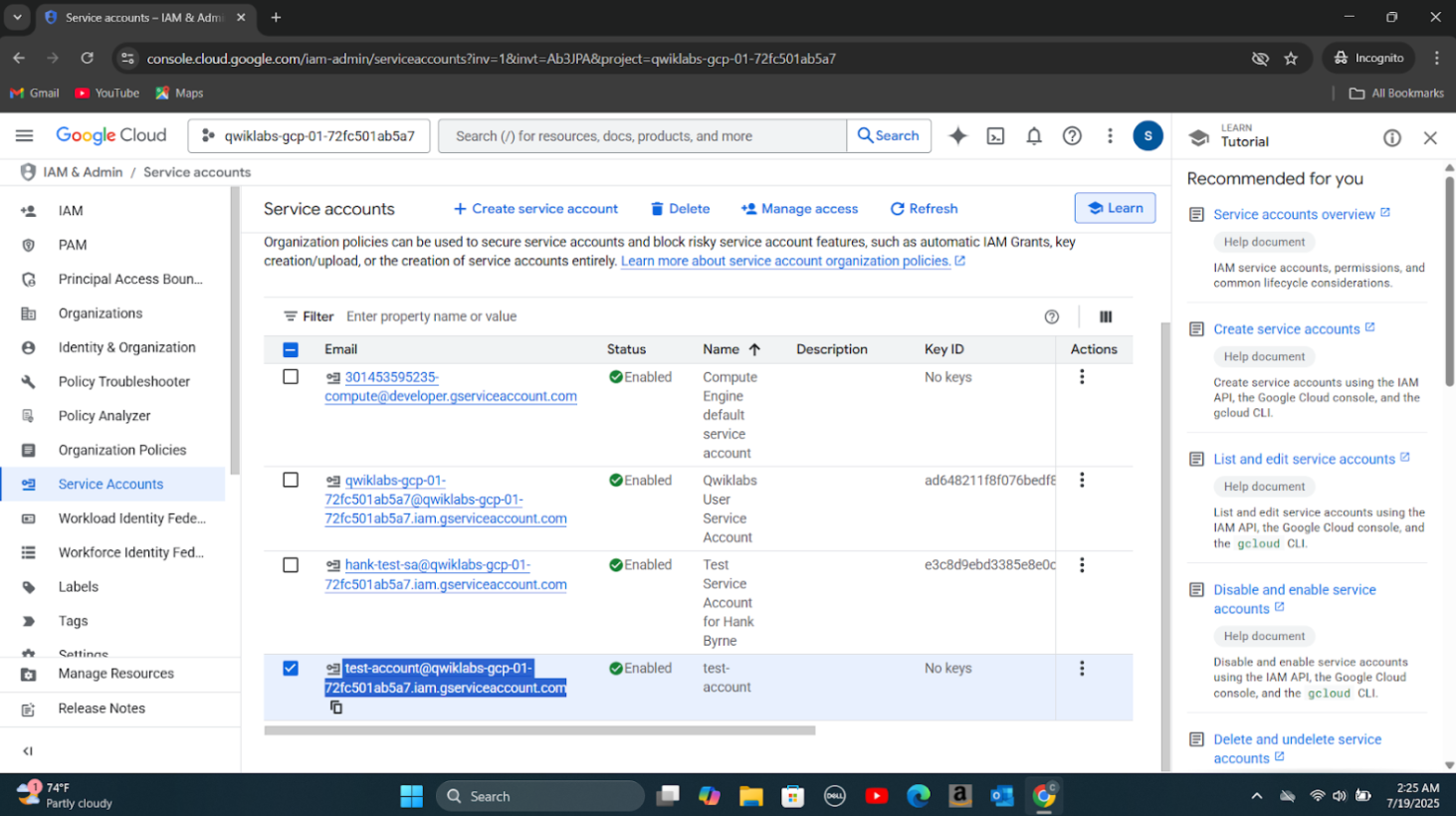
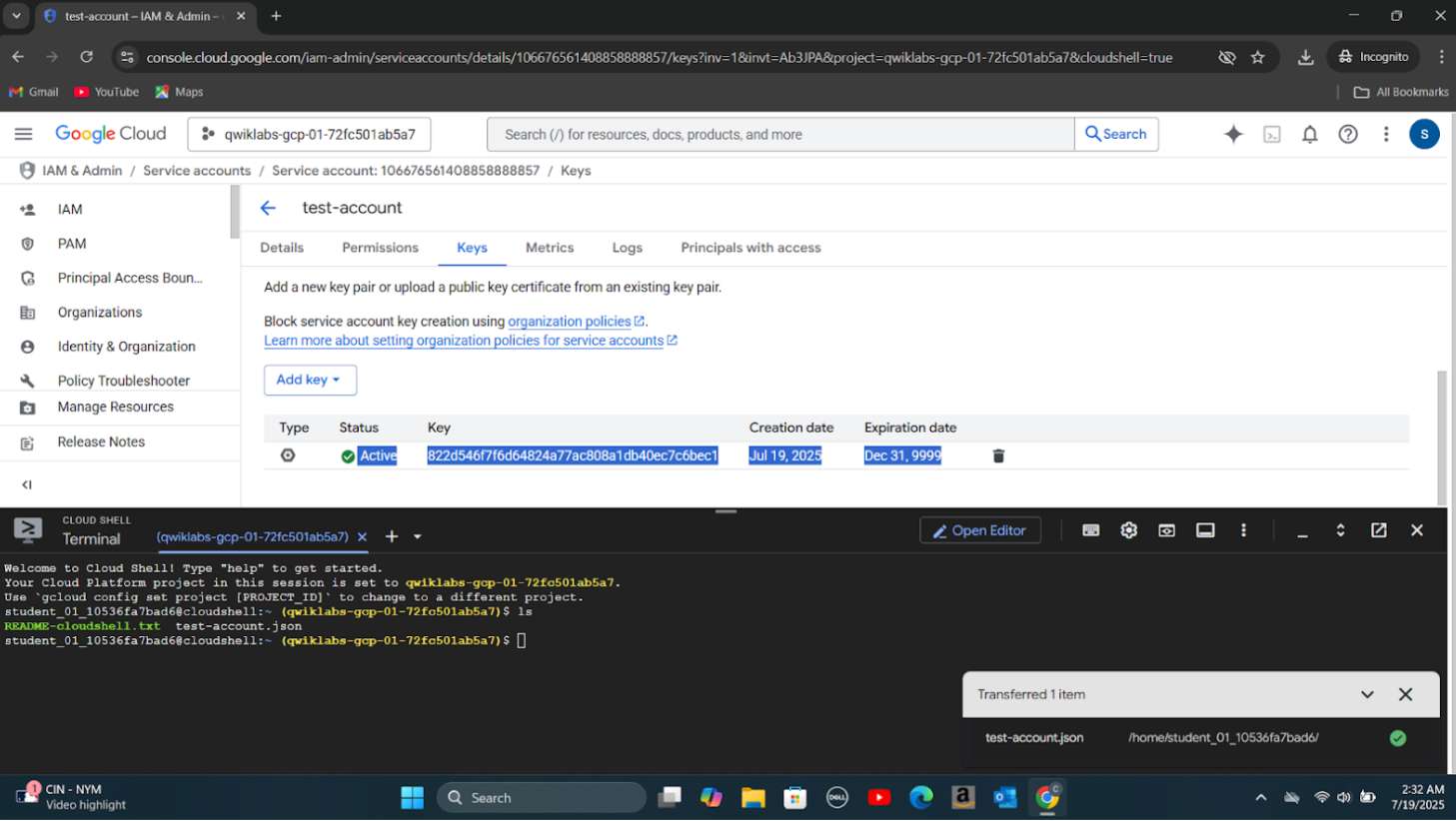
Step 1: Recreated the false positive by creating a service account(test-account), assigning a role, providing a key, and activating the service account.
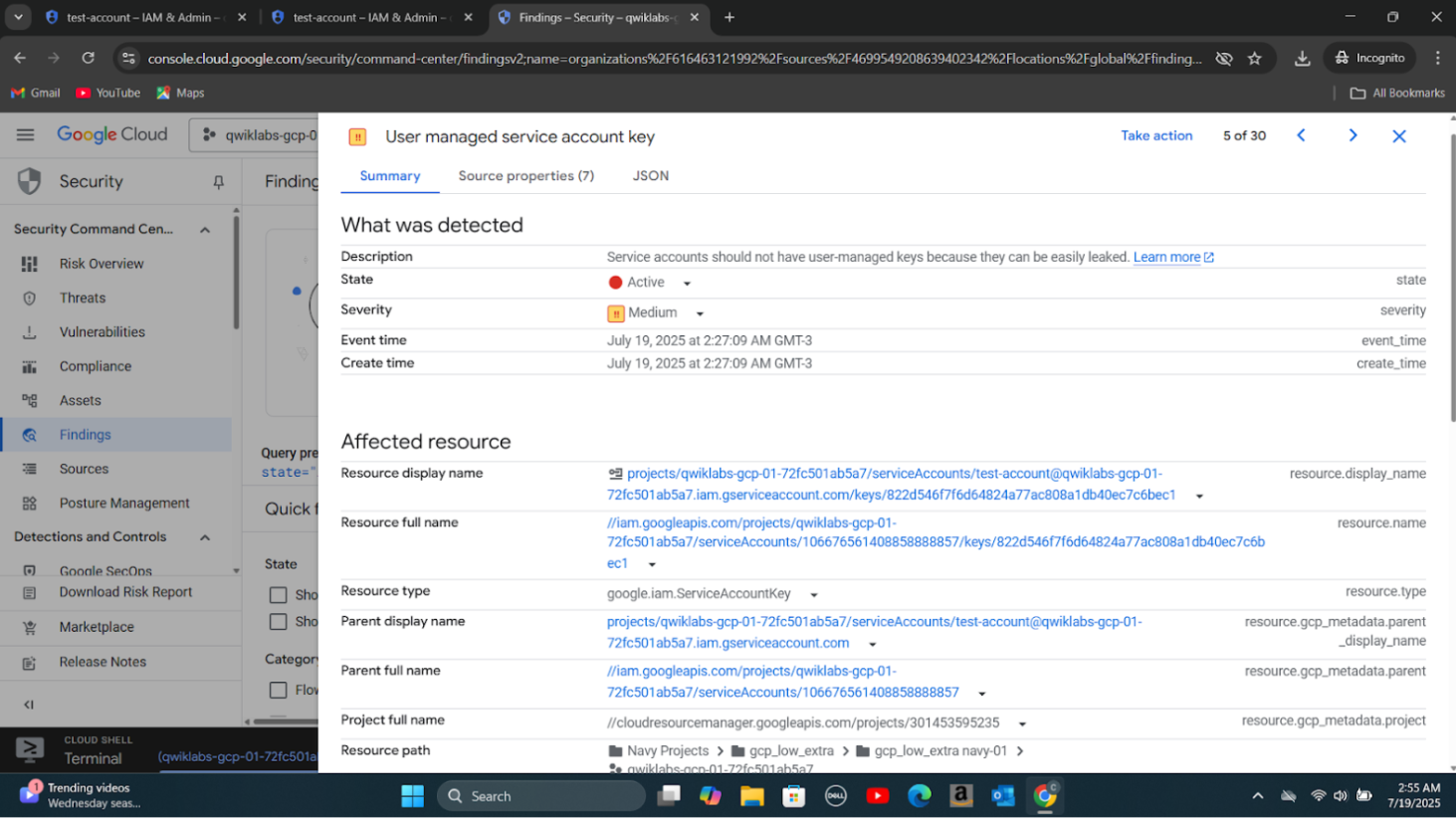
Step 2: Triggered a false positive finding and accessed the vulnerability finding related to the triggered activity in Security Command Center.
Step 3: Analyzed the finding and took remediation action to close the alert(deleting a service account key) and prevent future false positives.
Tools
Google Cloud Security Command Center, IAM, Cloud Logging
Frameworks
Cloud Threat Detection & Response, Least Privilege Principle
Standards
ISO 27001, NIST CSF