Investigating and Remediating IAM Threat Findings
Recreated malicious IAM activity, analyzed Security Command Center findings, and remediated improper IAM configurations to distinguish benign activity from true security incidents.
Steps
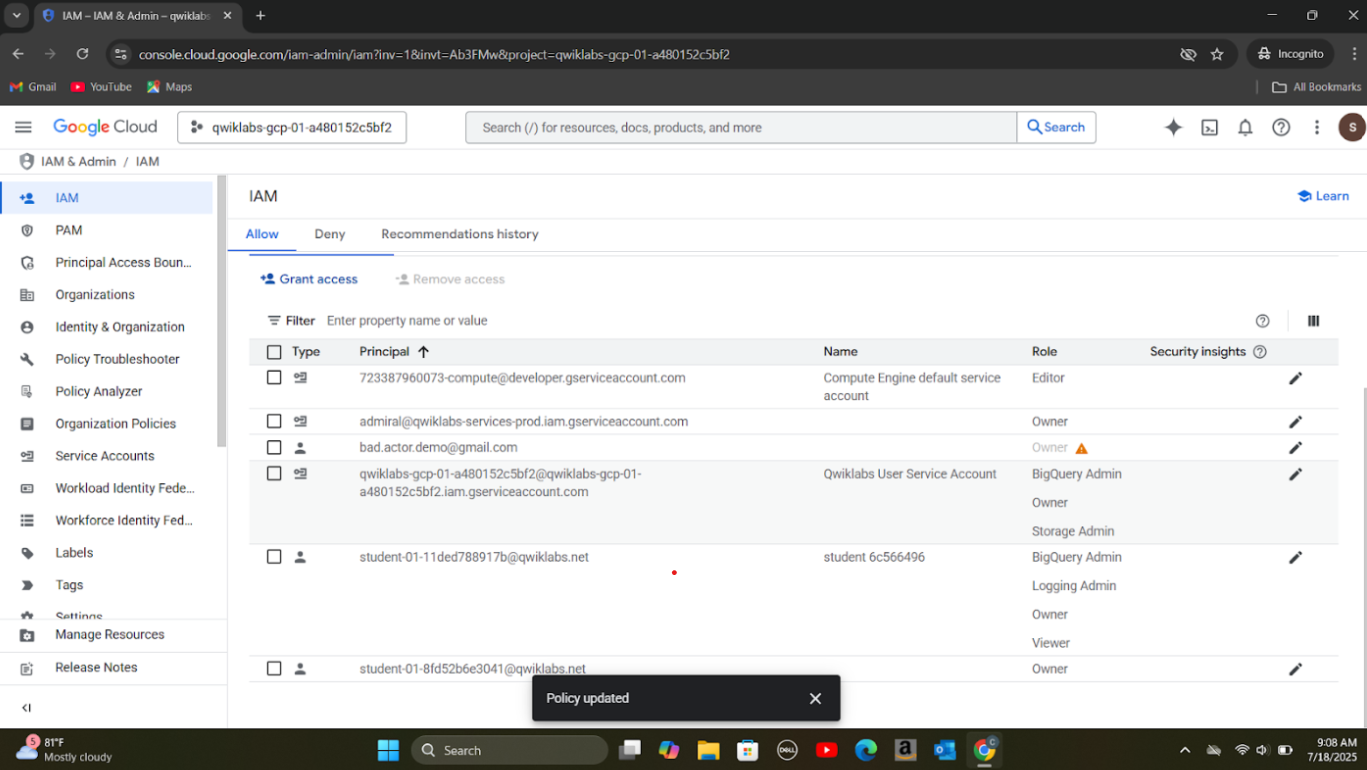
Step 1: Granted permissions to an external account-bad.actor.demo to intentionally trigger an IAM Event Threat Detection finding.
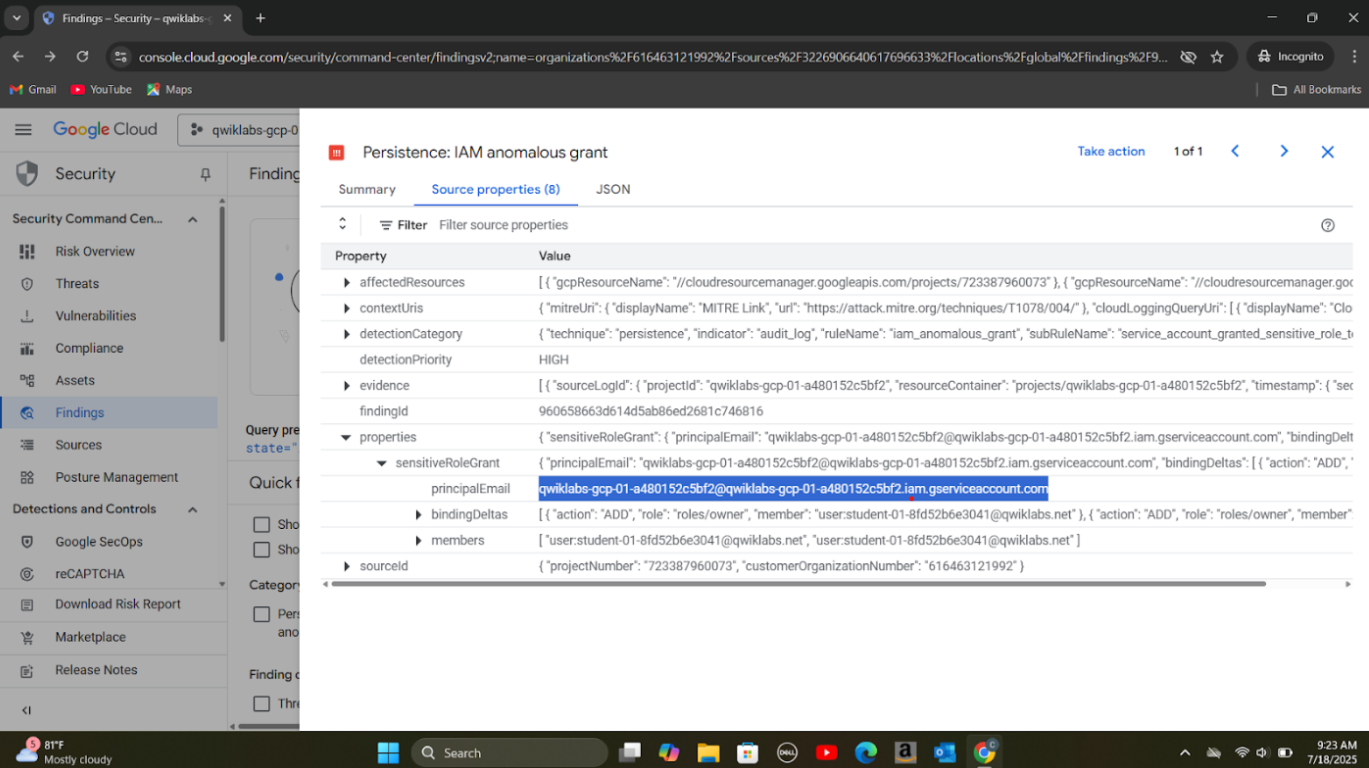
Step 2: Used Security Command Center to access and review the two IAM findings.
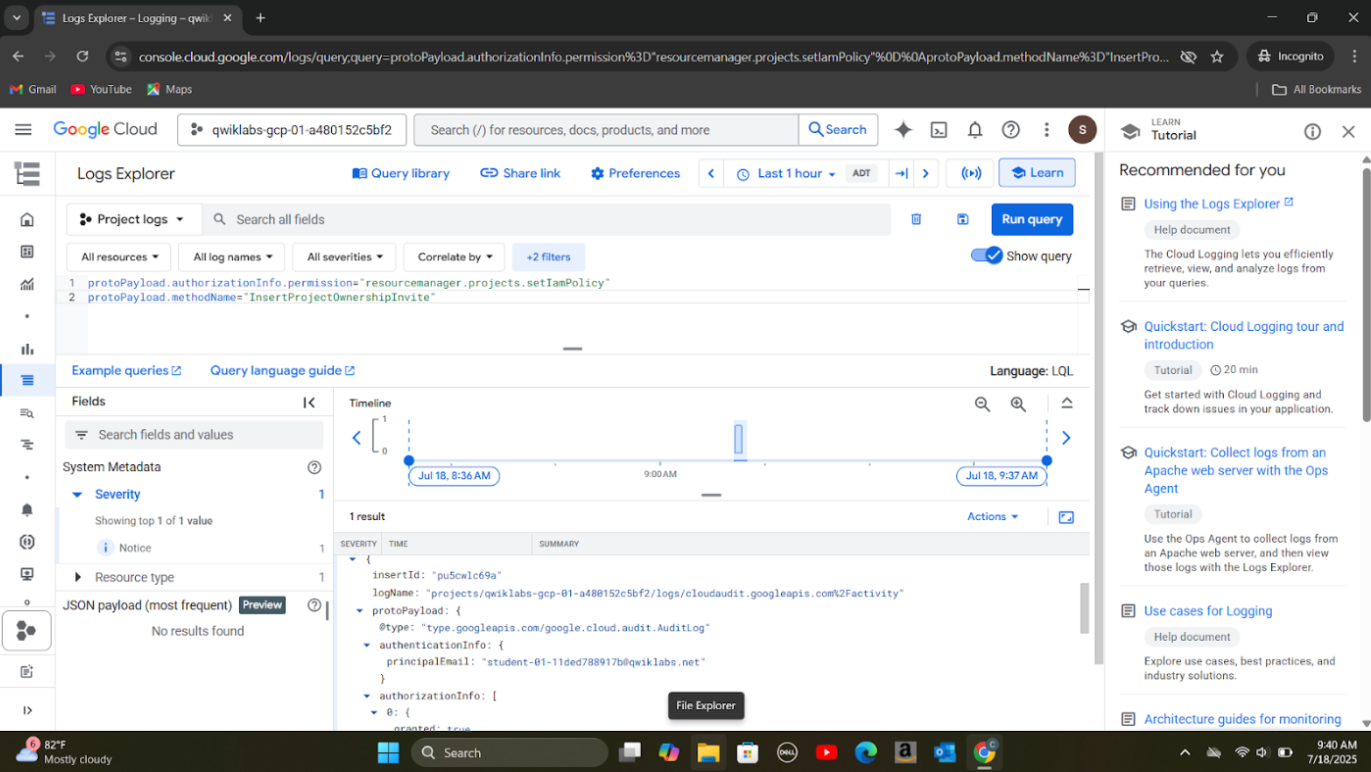
Step 3: Analyzed logs in Security Command Center and Cloud Logging to find out the principal that granted access.
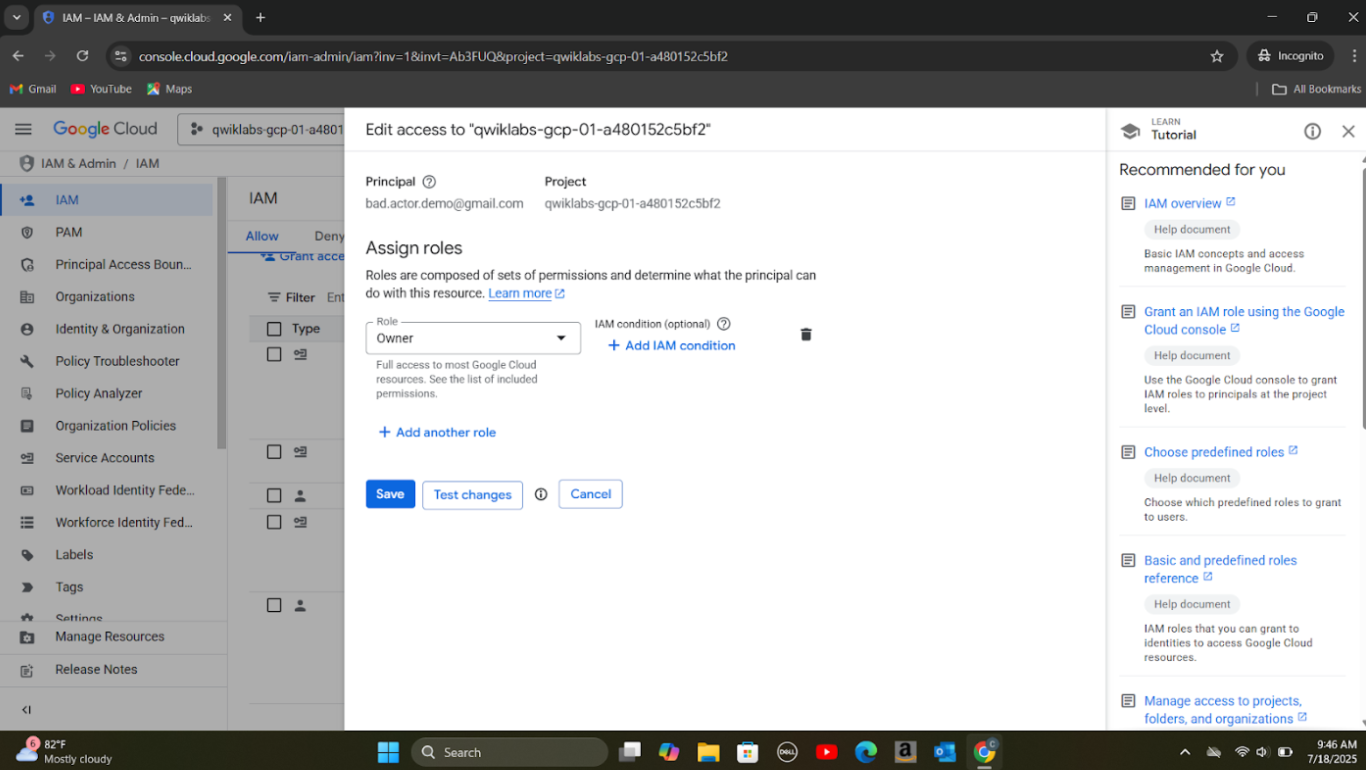
Step 4: Remediated the malicious finding by adjusting IAM settings and removing unauthorized permissions.
Tools
Google Cloud Security Command Center, Cloud Logging, IAM, Event Threat Detection
Frameworks
Zero Trust Architecture, Cloud Threat Detection & Response
Standards
ISO 27001, NIST CSF